Perot Systems - 5th to 11th Jan 2009 - Chennai - BPO careers for freshers
Posted: 07 Jan 2009 09:13 PM PST
WALK IN for exciting BPO careers for freshers (2008 batch graduates can also apply)
Venue:
Chennai
A9, 1st Main Road, Ambattur Industrial Estate, Chennai 600058
Ph: 044 42060330
Walkin time: 10.00 amto 5.00pm
Walk in with your resume and walk out with an offer letter
Desired Candidate Profile
- Graduates / Post-graduates in any discipline
- Strong analytical and typing skills (13WPM)
- Willingness to work in continuous night shifts.
Company Profile
At Perot Systems, we provide solutions that help global corporations achieve business-building results. Perot Systems is a Fortune 1000 corporation with over 23,000 associates across 135 locations and revenues of $2.6 billion in 2007.
TCS BPO - 5th to 9th Jan 2009 - Chennai - Banking Jobs
Posted: 07 Jan 2009 08:44 PM PST
Tata Consultancy Services (TCS) is one of the world's leading information technology companies. Through its Global Network Delivery Model, Innovation Network, and Solution Accelerators, TCS focuses on helping global organizations address their business challenges effectively.
TCS continues to invest in new technologies, processes, and people which can help its customers succeed. From generating novel concepts through TCS Innovation Labs and academic alliances, to drawing on the expertise of key partners, it keeps clients operating at the very edge of technological possibility. .
Whether TCS is envisioning a business advantage, engineering an IT and ITES solution, or executing an outsourcing strategy, it helps its customers experience certainty in their every day business.
TCS reported 2007-08 global revenues of USD 5.7 billion.
Designation
Banking Jobs - TCS BPO
Job Description
Should be Open fior Night Shifts
Should have Excellent communication skills
Should have Financial Background
Desired Profile
Role- Team Member
Reconcilement of daily bank statement activity to sub ledger activity
Capturing data for MI reports.
Qualities check all requests with a high degree of accuracy while adhering to company policies and Industry standards.
Keep up to date with e-mails and procedure notices
Research process and QC errors to determine validity and use as a learning experience
Requirement:
Fresher & Experienced in any Domain,
Exposure in Backend Support.
Should be willing to work in shifts.
Interested Candidates can Walk-in with a hard copy of your CV, copy of last 2 months pay slip from current company and Relieving letter from Previous company (If you are experienced) and one passport size photograph(Mandator y).
Work Location: Chennai
Venue:
Tata Consultancy Services Limited,
165/1A, Velachery to Taramani 100 feet road,
Velachery, Chennai â€" 600 042.
Near Vijaya Nagar Bus Stop
Day : 5th to 9th Jan 2009
Registration Time: 11AM â€" 1PM
Contact Person: Kalvath
Note:
BE/B.Tech/MCA need not apply
Please bring a Xerox copy of this mail for the reference (Mandatory)
Should have 15 years of Regular Education
Candidates attended interview within 6 months will not be Eligible.
Experience 0 - 4 Years
Industry Type BPO/ITES /CRM/Transcription
Functional Area ITES/BPO/KPO, Customer Service, Ops.
Education UG - B.B.A - Management,B. Com - Commerce
PG - CA,ICWA,M.Com - Commerce,MBA/ PGDM - Any Specialization
Location Chennai
Keywords BPO , Non - voice , Finance, Banking, Fund, Hedge, Reconciliation, TCS, Back - end support , BCOM, Commerce, Accounts, Insurance, Freshers
Contact Kalvath
Tata Consultancy Services
Friday, January 9, 2009
Wednesday, January 7, 2009
Job Motivation Quotes
“We shall neither fail nor falter; we shall not weaken or tire...give us the tools and we will finish the job.”
Whenever it is possible, a boy should choose some occupation which he should do even if he did not need the money.
Don't waste time learning the "tricks of the trade." Instead, learn the trade.
“Why compare yourself with others? No one in the entire world can do a better job of being you than you.”
There are no menial jobs, only menial attitudes.
Choose a job you love, and you will never have to work a day in your life.
By working faithfully eight hours a day you may eventually get to be boss and work twelve hours a day.
“When you are asked if you can do a job, tell 'em, 'Certainly I can!' Then get busy and find out how to do it.”
“I think the person who takes a job in order to live - that is to say, for the money - has turned himself into a slave.”
“You can't do today's job with yesterday's methods and be in business tomorrow”
Whenever it is possible, a boy should choose some occupation which he should do even if he did not need the money.
Don't waste time learning the "tricks of the trade." Instead, learn the trade.
“Why compare yourself with others? No one in the entire world can do a better job of being you than you.”
There are no menial jobs, only menial attitudes.
Choose a job you love, and you will never have to work a day in your life.
By working faithfully eight hours a day you may eventually get to be boss and work twelve hours a day.
“When you are asked if you can do a job, tell 'em, 'Certainly I can!' Then get busy and find out how to do it.”
“I think the person who takes a job in order to live - that is to say, for the money - has turned himself into a slave.”
“You can't do today's job with yesterday's methods and be in business tomorrow”
How to improve my Communication skills ?
Courtesy: www.neutralaccent.com
1.Listen and don't assume.
2.Exercise Emotional control.
3.Active Listening.
4.Interaction and Participation.
5.Practice Listening for better understanding.
6.Raise Good,Intellectual and Powerful questions.
7.Have an eye contact.
8.Listen with high energy level.
9.Improve body language.
10.Be in a normal and good mood.
11.Don't take things personally. 12.Concentrate inspite of distractions.
13.Avoid imagination, assumptions, and pre-judinging or pre-occupation.
14.Do not communicate with the intention of arguing, withdrawing, blaming, accusing and changing the subject.
15.Try to understand and not evaluate.
16.Build Rapport.
17.Have a purposeful listening. 18.Develop creative communication.
Monday, January 5, 2009
Networking Basics
NETWORKING
The first networks were time-sharing networks that used mainframes and attached terminals. Such environments were implemented by both IBM's System Network Architecture (SNA) and Digital's network architecture. Local area networks (LANs) evolved around the PC revolution and provide high-speed, fault-tolerant data networks that cover a relatively small geographic area or that is confined to a single building or group of buildings. They provide connected users with shared access to devices and applications and allow them to exchange files and communicate via electronic mail. Wide area networks (WANs) cover broader geographic areas, often using transmission facilities provided by common carriers, such as telephone companies, to interconnect a number of LANs.
Whilst LANs and WANs make up the majority of networks - indeed, the Internet can be correctly regarded as the largest WAN in existence - there are many different types of network, categorised by a number of distinguishing characteristics:
topology: the geometric arrangement of a computer system. Common topologies include a bus, star, and ring
standards/protocols: definitions of common sets of rules and signals that specify how computers on a network communicate. Ethernet and Token Ring are examples of network cabling standards, whilst TCP/IP is the predominant network communications protocol
architecture: networks can be broadly classified as using either a peer-to-peer or client-server architecture.
In addition to the computers themselves, sometimes referred to as nodes, the implementation of a network involves:
a device on each connected computer that enables it to communicate with the network, usually called a network interface card (NIC)
various items of specialist network hardware, including devices to act as connection points between the various nodes, generally referred to as hubs or switches
a connection medium, usually a wire or cable, although wireless communication between networked computers is increasingly common.
The Open Systems Interconnection (OSI) reference model describes how information from a software application in one computer moves through a network medium to a software application in another computer. The OSI reference model is a conceptual model composed of seven layers, each specifying particular network functions. The model was developed by the International Organisation for Standardisation (ISO) in 1984, and it is now considered the primary architectural model for intercomputer communications. The OSI model divides the tasks involved with moving information between networked computers into seven smaller, more manageable task groups. A task or group of tasks is then assigned to each of the seven OSI layers. Each layer is reasonably self-contained, so that the tasks assigned to each layer can be implemented independently. This enables the solutions offered by one layer to be updated without adversely affecting the other layers.
The seven layers of the OSI reference model can be divided into two categories: upper layers and lower layers. The upper layers of the OSI model deal with application issues and generally are implemented only in software. The highest layer, application, is closest to the end user. Both users and application-layer processes interact with software applications that contain a communications component. The term upper layer is sometimes used to refer to any layer above another layer in the OSI model. The lower layers of the OSI model handle data transport issues. The physical layer and data link layer are implemented in hardware and software. The other lower layers generally are implemented only in software. The lowest layer, the physical layer, is closest to the physical network medium (the network cabling, for example) , and is responsible for actually placing information on the medium.
Reference Layer Function
7 Application Layer Application programs that use the network
6 Presentation Layer Standardises data presented to the applications
5 Session Layer Manages sessions between applications
4 Transport Layer Provides error detection and correction
3 Network Layer Manages network connections
2 Data Link Layer Provides data delivery across the physical connection
1 Physical Layer Defines the physical network media
LAN topologies define the manner in which network devices are organised. Four common LAN topologies exist:
A bus topology is a linear LAN architecture in which transmissions from network stations propagate the length of the medium and are received by all other stations. Many nodes can tap into the bus and begin communication with all other nodes on that cable segment. A break anywhere in the cable will usually cause the entire segment to be inoperable until the break is repaired. Of the three most widely used LAN implementations, Standard Ethernet/IEEE 802.3 networks implement a bus topology in which all devices are connected to a central cable, called the bus or backbone.
A ring topology is a LAN architecture in which all devices are connected to one another in the shape of a closed loop, so that each device is connected directly to two other devices, one on either side of it. Both Token Ring/IEEE 802.5 and FDDI networks implement a ring topology.
A star topology is a LAN architecture in which the endpoints on a network are connected to a common central hub, or switch, by dedicated links. 10BaseT Ethernet uses a star topology, generally with a computer being located at one end of the segment, and the other end being terminated with a hub. The primary advantage of this type of network is reliability - if one "point-to-point" segments has a break, it will only affect the nodes on that link; other computer users on the network continue to operate as if that segment were non-existent.
A tree topology is a LAN architecture that is identical to the bus topology, except that branches with multiple nodes are possible in this case.
These topologies are logical architectures and the way in which devices are physically organised can mix topologies. For example, a star-wired bus network - as used by 10BaseT Ethernet - typically consists of a high-bandwidth backbone bus which connects to a collection of slower-bandwidth star segments.
These topologies are logical architectures and the way in which devices are physically organised can mix topologies. For example, a 10BaseT network's use of a hub effectively transforms a standard bus topology to a "star-wired bus" topology. A network comprising a high-bandwidth backbone bus which connects to a collection of slower-bandwidth star segments is another common example of this type of mixed topology.
Of the three most widely used LAN implementations, both Fibre Distributed Data Interface (FDDI) and Token Ring/IEEE 802.5 networks implement a ring topology and Ethernet/IEEE 802.3 networks implement a bus topology.
Client-server networking architectures became popular in the late 1980s and early 1990s as many applications were migrated from centralised minicomputers and mainframes to networks of personal computers. The design of applications for a distributed computing environment required that they effectively be divided into two parts: client (front end) and server (back end). The network architecture on which they were implemented mirrored this client-server model, with a user's PC (the client) typically acting as the requesting machine and a more powerful server machine - to which it was connected via either a LAN or a WAN - acting as the supplying machine.
Their inherent scaleability make client-server networks suitable for mid-sized and large businesses, with servers ranging in capacity from high-end PCs to mainframes, as appropriate. Client-server networks require special Network Operating System (NOS) software in addition to the normal operating system software.
With the price of PCs falling at the same time the advantages for consumers to being connected - online investing and shopping, keeping in touch with long-distance friends and relatives, enjoying multiplayer games and tapping the vast resources of the Internet - continued to multiply, it was no surprise that by the late 1990s computer networking was being propelled from its traditional corporate base into a brave new world - the home.
However, with an increasing number of households owning two or more PCs - forecasts predicted that more than 30 million North American households would own two or more computers by the end of 2002 - they found themselves experiencing the same limitations that confronted businesses almost 20 years earlier: the inability to share computing and peripheral resources or to share information easily between computer users.
The four most compelling home network market drivers are:
Simultaneous high-speed Internet access using a single ISP account: As the Internet becomes an essential tool in business, education, medicine and government, as well as our personal lives, the demand for high-speed, convenient, easily accessible Internet access is mushrooming. Cable, ISDN, and digital subscriber line (DSL) modems provide the fastest Internet connections and allow family members to talk on the phone and use the Internet simultaneously.
Peripheral sharing: Families want to get the most out of their computer equipment investments by sharing the same printers, modems, or other peripherals from any PC in the home.
Sharing files and applications: Families also want to maximise the value of their software investments by sharing applications, and they want the convenience of sharing files easily, without having to transfer from machine to machine via floppies or CDs.
Entertainment: The new wave of multiplayer computer games, with their advanced graphics and exciting audio tracks, are beginning to grab consumer interest. Many analysts believe that PC games and entertainment software represent the swiftest long-term growth segment of the overall U.S. electronic gaming marketplace, with a combined unit annual growth rate of 24% being predicted between 1997 and 2002. The two biggest growth factors are the continuing price drop in home PCs and the opportunity for multiplayer gaming.
The solution for home users in the late 1990s is the same as it had been for corporate users more than a decade earlier: networking.
While consumer demand has swelled, recent advances have overcome the technological and complexity barriers that once prevented networking from migrating into nontechnical environments. Component prices have dropped, available network speeds have accelerated, and signal attenuation and noise problems have been addressed using low-cost, high-performance signal processing. However, success in the consumer market requires that home networks be inexpensive, easy to install and easy to use. Essentially, that means the technology must be transparent to the user.
By the early 2000s, home networking technologies had made significant progress towards meeting these requirements, providing consumers with an impressive array of options. The wired network technologies use some form of physical cabling to connect computing devices, the choice being between Ethernet, phoneline and powerline. Wireless networks, on the other hand, use electromagnetic airwaves - infrared or radio - to transmit information from one point to another.
As with the others, the technology for wireless networks has also been around for some time, achieving a measure of success during the late 1990s in a number of vertical markets, including health-care, retail and manufacturing. Home networking simply takes the technology to another level of functionality.
Wireless LANs (WLANs) can now offer the same advantages to consumers: first and foremost is mobility. Consumers have the flexibility to move inside or outside their homes and still remain connected to the Internet or to other computing devices on the network. Installation is easy because there are no wires. Wireless network components can be set up anywhere in the home. Wireless networking makes it easy to move computers and other devices without the need to reconfigure the network.
Wireless LANs use electromagnetic airwaves, either infrared IrDA) or radio frequency (RF), to communicate information from one point to another without relying on any physical connection. Radio waves are often referred to as radio carriers because they simply perform the function of delivering energy to a remote receiver. The data being transmitted is superimposed on the radio carrier so that it can be accurately extracted at the receiving end. This is generally referred to as modulation of the carrier by the information being transmitted. Once data is superimposed (modulated) onto the radio carrier, the radio signal occupies more than a single frequency, since the frequency or bit rate of the modulating information adds to the carrier.
Multiple radio carriers can exist in the same space at the same time without interfering with each other if the radio waves are transmitted on different radio frequencies. To extract data, a radio receiver or augment networks without installing or moving wires. Wireless LANs tunes in (or selects) one radio frequency while rejecting all other radio signals on different frequencies.
In a typical WLAN configuration, a transmitter/receiver (transceiver) device, called an Access Point (AP), connects to the wired network from a fixed location using standard Ethernet cable. At a minimum, the Access Point receives, buffers, and transmits data between the WLAN and the wired network infrastructure. A single Access Point can support a small group of users and can function within a range of less than one hundred to several hundred feet. The Access Point (or the antenna attached to the access point) is usually mounted high but may be mounted essentially anywhere that is practical as long as the desired radio coverage is obtained.
End users access the WLAN through wireless-LAN adapters, which are implemented as PCMCIA cards in notebook computers, ISA or PCI cards in desktop computers, or integrated within hand-held computers. WLAN adapters provide an interface between the client network operating system (NOS) and the airwaves (via an antenna). The nature of the wireless connection is transparent to the NOS.
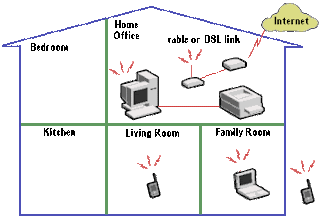
The figure shows how a wireless network could be set up in the home. Internal or external adapters are installed on each PC. Printers or other peripherals can be shared through a connected PC. The devices then communicate using a set of reserved high-frequency radiowaves. An access point device connects to a DSL or cable modem and enables high-rate (broadband) Internet access for the entire network.
Because RF-based wireless home networking technology is not restricted by line-of-sight, network components do not need to be located in the same room to communicate. In a typical home, the maximum distance between devices is about 250 feet. Family members can wander from room to room or relax on the patio while surfing the Internet from their laptops.
Several wireless networking standards exist, including Bluetooth, HomeRF and IEEE 802.11, but each serves different purposes. Bluetooth is a technology to connect devices without wires. The intended use is to provide short-range connections between mobile devices and to the Internet via bridging devices to different networks (wired and wireless) that provide Internet capability. HomeRF SWAP is a wireless technology optimised for the home environment. Its primary use is to provide data networking and dial tones between devices such as PCs, cordless phones, Web Tablets, and a broadband cable or DSL modem. Both technologies share the same frequency spectrum but do not interfere when operating in the same space. Both Bluetooth and HomeRF functionality can be implemented in the same device. IEEE 802.11 is emerging as the primary standard for wireless network and Internet access. It supports 11 Mbit/s wireless access in the 2.4GHz radio band and works over longer distances than Bluetooth and HomeRF.
Routers
Routing achieved commercial popularity in the mid-1980s - at a time when large-scale internetworking began to replace the fairly simple, homogeneous environments that had been the norm hitherto. Routing is the act of moving information across an internetwork from a source to a destination. It is often contrasted with bridging, which performs a similar function. The primary difference between the two is that bridging occurs at Layer 2 (the link layer) of the OSI reference model, whereas routing occurs at Layer 3 (the network layer). This distinction provides routing and bridging with different information to use in the process of moving information from source to destination, so the two functions accomplish their tasks in different ways.

Routers use information within each packet to route it from one LAN to another, and communicate with each other and share information that allows them to determine the best route through a complex network of many LANs. To do this, routers build and maintain "routing tables", which contain various items of route information - depending on the particular routing algorithm used. For example, destination/next hop associations tell a router that a particular destination can be gained optimally by sending the packet to a particular router representing the "next hop" on the way to the final destination. When a router receives an incoming packet, it checks the destination address and attempts to associate this address with a next hop.
The first networks were time-sharing networks that used mainframes and attached terminals. Such environments were implemented by both IBM's System Network Architecture (SNA) and Digital's network architecture. Local area networks (LANs) evolved around the PC revolution and provide high-speed, fault-tolerant data networks that cover a relatively small geographic area or that is confined to a single building or group of buildings. They provide connected users with shared access to devices and applications and allow them to exchange files and communicate via electronic mail. Wide area networks (WANs) cover broader geographic areas, often using transmission facilities provided by common carriers, such as telephone companies, to interconnect a number of LANs.
Whilst LANs and WANs make up the majority of networks - indeed, the Internet can be correctly regarded as the largest WAN in existence - there are many different types of network, categorised by a number of distinguishing characteristics:
topology: the geometric arrangement of a computer system. Common topologies include a bus, star, and ring
standards/protocols: definitions of common sets of rules and signals that specify how computers on a network communicate. Ethernet and Token Ring are examples of network cabling standards, whilst TCP/IP is the predominant network communications protocol
architecture: networks can be broadly classified as using either a peer-to-peer or client-server architecture.
In addition to the computers themselves, sometimes referred to as nodes, the implementation of a network involves:
a device on each connected computer that enables it to communicate with the network, usually called a network interface card (NIC)
various items of specialist network hardware, including devices to act as connection points between the various nodes, generally referred to as hubs or switches
a connection medium, usually a wire or cable, although wireless communication between networked computers is increasingly common.
The Open Systems Interconnection (OSI) reference model describes how information from a software application in one computer moves through a network medium to a software application in another computer. The OSI reference model is a conceptual model composed of seven layers, each specifying particular network functions. The model was developed by the International Organisation for Standardisation (ISO) in 1984, and it is now considered the primary architectural model for intercomputer communications. The OSI model divides the tasks involved with moving information between networked computers into seven smaller, more manageable task groups. A task or group of tasks is then assigned to each of the seven OSI layers. Each layer is reasonably self-contained, so that the tasks assigned to each layer can be implemented independently. This enables the solutions offered by one layer to be updated without adversely affecting the other layers.
The seven layers of the OSI reference model can be divided into two categories: upper layers and lower layers. The upper layers of the OSI model deal with application issues and generally are implemented only in software. The highest layer, application, is closest to the end user. Both users and application-layer processes interact with software applications that contain a communications component. The term upper layer is sometimes used to refer to any layer above another layer in the OSI model. The lower layers of the OSI model handle data transport issues. The physical layer and data link layer are implemented in hardware and software. The other lower layers generally are implemented only in software. The lowest layer, the physical layer, is closest to the physical network medium (the network cabling, for example) , and is responsible for actually placing information on the medium.
Reference Layer Function
7 Application Layer Application programs that use the network
6 Presentation Layer Standardises data presented to the applications
5 Session Layer Manages sessions between applications
4 Transport Layer Provides error detection and correction
3 Network Layer Manages network connections
2 Data Link Layer Provides data delivery across the physical connection
1 Physical Layer Defines the physical network media
LAN topologies define the manner in which network devices are organised. Four common LAN topologies exist:
A bus topology is a linear LAN architecture in which transmissions from network stations propagate the length of the medium and are received by all other stations. Many nodes can tap into the bus and begin communication with all other nodes on that cable segment. A break anywhere in the cable will usually cause the entire segment to be inoperable until the break is repaired. Of the three most widely used LAN implementations, Standard Ethernet/IEEE 802.3 networks implement a bus topology in which all devices are connected to a central cable, called the bus or backbone.
A ring topology is a LAN architecture in which all devices are connected to one another in the shape of a closed loop, so that each device is connected directly to two other devices, one on either side of it. Both Token Ring/IEEE 802.5 and FDDI networks implement a ring topology.
A star topology is a LAN architecture in which the endpoints on a network are connected to a common central hub, or switch, by dedicated links. 10BaseT Ethernet uses a star topology, generally with a computer being located at one end of the segment, and the other end being terminated with a hub. The primary advantage of this type of network is reliability - if one "point-to-point" segments has a break, it will only affect the nodes on that link; other computer users on the network continue to operate as if that segment were non-existent.
A tree topology is a LAN architecture that is identical to the bus topology, except that branches with multiple nodes are possible in this case.
These topologies are logical architectures and the way in which devices are physically organised can mix topologies. For example, a star-wired bus network - as used by 10BaseT Ethernet - typically consists of a high-bandwidth backbone bus which connects to a collection of slower-bandwidth star segments.
These topologies are logical architectures and the way in which devices are physically organised can mix topologies. For example, a 10BaseT network's use of a hub effectively transforms a standard bus topology to a "star-wired bus" topology. A network comprising a high-bandwidth backbone bus which connects to a collection of slower-bandwidth star segments is another common example of this type of mixed topology.
Of the three most widely used LAN implementations, both Fibre Distributed Data Interface (FDDI) and Token Ring/IEEE 802.5 networks implement a ring topology and Ethernet/IEEE 802.3 networks implement a bus topology.
Client-server networking architectures became popular in the late 1980s and early 1990s as many applications were migrated from centralised minicomputers and mainframes to networks of personal computers. The design of applications for a distributed computing environment required that they effectively be divided into two parts: client (front end) and server (back end). The network architecture on which they were implemented mirrored this client-server model, with a user's PC (the client) typically acting as the requesting machine and a more powerful server machine - to which it was connected via either a LAN or a WAN - acting as the supplying machine.
Their inherent scaleability make client-server networks suitable for mid-sized and large businesses, with servers ranging in capacity from high-end PCs to mainframes, as appropriate. Client-server networks require special Network Operating System (NOS) software in addition to the normal operating system software.
With the price of PCs falling at the same time the advantages for consumers to being connected - online investing and shopping, keeping in touch with long-distance friends and relatives, enjoying multiplayer games and tapping the vast resources of the Internet - continued to multiply, it was no surprise that by the late 1990s computer networking was being propelled from its traditional corporate base into a brave new world - the home.
However, with an increasing number of households owning two or more PCs - forecasts predicted that more than 30 million North American households would own two or more computers by the end of 2002 - they found themselves experiencing the same limitations that confronted businesses almost 20 years earlier: the inability to share computing and peripheral resources or to share information easily between computer users.
The four most compelling home network market drivers are:
Simultaneous high-speed Internet access using a single ISP account: As the Internet becomes an essential tool in business, education, medicine and government, as well as our personal lives, the demand for high-speed, convenient, easily accessible Internet access is mushrooming. Cable, ISDN, and digital subscriber line (DSL) modems provide the fastest Internet connections and allow family members to talk on the phone and use the Internet simultaneously.
Peripheral sharing: Families want to get the most out of their computer equipment investments by sharing the same printers, modems, or other peripherals from any PC in the home.
Sharing files and applications: Families also want to maximise the value of their software investments by sharing applications, and they want the convenience of sharing files easily, without having to transfer from machine to machine via floppies or CDs.
Entertainment: The new wave of multiplayer computer games, with their advanced graphics and exciting audio tracks, are beginning to grab consumer interest. Many analysts believe that PC games and entertainment software represent the swiftest long-term growth segment of the overall U.S. electronic gaming marketplace, with a combined unit annual growth rate of 24% being predicted between 1997 and 2002. The two biggest growth factors are the continuing price drop in home PCs and the opportunity for multiplayer gaming.
The solution for home users in the late 1990s is the same as it had been for corporate users more than a decade earlier: networking.
While consumer demand has swelled, recent advances have overcome the technological and complexity barriers that once prevented networking from migrating into nontechnical environments. Component prices have dropped, available network speeds have accelerated, and signal attenuation and noise problems have been addressed using low-cost, high-performance signal processing. However, success in the consumer market requires that home networks be inexpensive, easy to install and easy to use. Essentially, that means the technology must be transparent to the user.
By the early 2000s, home networking technologies had made significant progress towards meeting these requirements, providing consumers with an impressive array of options. The wired network technologies use some form of physical cabling to connect computing devices, the choice being between Ethernet, phoneline and powerline. Wireless networks, on the other hand, use electromagnetic airwaves - infrared or radio - to transmit information from one point to another.
As with the others, the technology for wireless networks has also been around for some time, achieving a measure of success during the late 1990s in a number of vertical markets, including health-care, retail and manufacturing. Home networking simply takes the technology to another level of functionality.
Wireless LANs (WLANs) can now offer the same advantages to consumers: first and foremost is mobility. Consumers have the flexibility to move inside or outside their homes and still remain connected to the Internet or to other computing devices on the network. Installation is easy because there are no wires. Wireless network components can be set up anywhere in the home. Wireless networking makes it easy to move computers and other devices without the need to reconfigure the network.
Wireless LANs use electromagnetic airwaves, either infrared IrDA) or radio frequency (RF), to communicate information from one point to another without relying on any physical connection. Radio waves are often referred to as radio carriers because they simply perform the function of delivering energy to a remote receiver. The data being transmitted is superimposed on the radio carrier so that it can be accurately extracted at the receiving end. This is generally referred to as modulation of the carrier by the information being transmitted. Once data is superimposed (modulated) onto the radio carrier, the radio signal occupies more than a single frequency, since the frequency or bit rate of the modulating information adds to the carrier.
Multiple radio carriers can exist in the same space at the same time without interfering with each other if the radio waves are transmitted on different radio frequencies. To extract data, a radio receiver or augment networks without installing or moving wires. Wireless LANs tunes in (or selects) one radio frequency while rejecting all other radio signals on different frequencies.
In a typical WLAN configuration, a transmitter/receiver (transceiver) device, called an Access Point (AP), connects to the wired network from a fixed location using standard Ethernet cable. At a minimum, the Access Point receives, buffers, and transmits data between the WLAN and the wired network infrastructure. A single Access Point can support a small group of users and can function within a range of less than one hundred to several hundred feet. The Access Point (or the antenna attached to the access point) is usually mounted high but may be mounted essentially anywhere that is practical as long as the desired radio coverage is obtained.
End users access the WLAN through wireless-LAN adapters, which are implemented as PCMCIA cards in notebook computers, ISA or PCI cards in desktop computers, or integrated within hand-held computers. WLAN adapters provide an interface between the client network operating system (NOS) and the airwaves (via an antenna). The nature of the wireless connection is transparent to the NOS.

The figure shows how a wireless network could be set up in the home. Internal or external adapters are installed on each PC. Printers or other peripherals can be shared through a connected PC. The devices then communicate using a set of reserved high-frequency radiowaves. An access point device connects to a DSL or cable modem and enables high-rate (broadband) Internet access for the entire network.
Because RF-based wireless home networking technology is not restricted by line-of-sight, network components do not need to be located in the same room to communicate. In a typical home, the maximum distance between devices is about 250 feet. Family members can wander from room to room or relax on the patio while surfing the Internet from their laptops.
Several wireless networking standards exist, including Bluetooth, HomeRF and IEEE 802.11, but each serves different purposes. Bluetooth is a technology to connect devices without wires. The intended use is to provide short-range connections between mobile devices and to the Internet via bridging devices to different networks (wired and wireless) that provide Internet capability. HomeRF SWAP is a wireless technology optimised for the home environment. Its primary use is to provide data networking and dial tones between devices such as PCs, cordless phones, Web Tablets, and a broadband cable or DSL modem. Both technologies share the same frequency spectrum but do not interfere when operating in the same space. Both Bluetooth and HomeRF functionality can be implemented in the same device. IEEE 802.11 is emerging as the primary standard for wireless network and Internet access. It supports 11 Mbit/s wireless access in the 2.4GHz radio band and works over longer distances than Bluetooth and HomeRF.
Routers
Routing achieved commercial popularity in the mid-1980s - at a time when large-scale internetworking began to replace the fairly simple, homogeneous environments that had been the norm hitherto. Routing is the act of moving information across an internetwork from a source to a destination. It is often contrasted with bridging, which performs a similar function. The primary difference between the two is that bridging occurs at Layer 2 (the link layer) of the OSI reference model, whereas routing occurs at Layer 3 (the network layer). This distinction provides routing and bridging with different information to use in the process of moving information from source to destination, so the two functions accomplish their tasks in different ways.

Routers use information within each packet to route it from one LAN to another, and communicate with each other and share information that allows them to determine the best route through a complex network of many LANs. To do this, routers build and maintain "routing tables", which contain various items of route information - depending on the particular routing algorithm used. For example, destination/next hop associations tell a router that a particular destination can be gained optimally by sending the packet to a particular router representing the "next hop" on the way to the final destination. When a router receives an incoming packet, it checks the destination address and attempts to associate this address with a next hop.
Email Tips 10
Tips
Write a meaningful subject line.
Keep the message focused and readable.
Identify yourself clearly.
Be kind -- don't flame.
Proofread.
Don't assume privacy.
Distinguish between formal and informal situations.
Respond Promptly.
Show Respect and Restraint.
Good Email Manners - here are some simple yet effective tips for using email more efficiently:
1. If you are sending an email to multiple people, put their email addresses in the BCC field and your own email address in the To: field. No one likes to share their private email address with strangers.
2. The email subject should be detailed enough to give the recipient an idea about the email content without having to open it. Single words like "Hi" or "Hello" or "Help" are a strict no-no. Think of meaningful but short titles.
3. Do not attach large attachments in your email since not everyone is on a broadband connection. If you have to send a large file over email, upload it to services like Yousendit and then pass on the link in the email.
4. If you have to email more than two documents as attachments, zip them in one file. Doing so would ensure that your friend won't miss downloading any file.
5. Do not write an email while you are drunk or in a really bad mood. It would reflect on the style of your writing.
6. Do not request a Read Notification Receipt.
7. Always reply to emails especially the ones specifically addressed to you. The sender is still waiting to hear from you.
8. Keep you email message short and to the point. Sentences like "I hope this email finds you alive and well" look good only in letter correspondence.
9. Do not hit the Send button without doing a spell check. An email with spelling mistakes or grammatical errors indicate that you have written the message in a non-serious mood and may convey a bad impression. Always read the message before broadcasting it to the world.
10. You may want to remove your personal mobile number and the home number from the email signature if you are participating in a big mailing list. You never know the kind of people who have subscribed to that list.
Write a meaningful subject line.
Keep the message focused and readable.
Identify yourself clearly.
Be kind -- don't flame.
Proofread.
Don't assume privacy.
Distinguish between formal and informal situations.
Respond Promptly.
Show Respect and Restraint.
Good Email Manners - here are some simple yet effective tips for using email more efficiently:
1. If you are sending an email to multiple people, put their email addresses in the BCC field and your own email address in the To: field. No one likes to share their private email address with strangers.
2. The email subject should be detailed enough to give the recipient an idea about the email content without having to open it. Single words like "Hi" or "Hello" or "Help" are a strict no-no. Think of meaningful but short titles.
3. Do not attach large attachments in your email since not everyone is on a broadband connection. If you have to send a large file over email, upload it to services like Yousendit and then pass on the link in the email.
4. If you have to email more than two documents as attachments, zip them in one file. Doing so would ensure that your friend won't miss downloading any file.
5. Do not write an email while you are drunk or in a really bad mood. It would reflect on the style of your writing.
6. Do not request a Read Notification Receipt.
7. Always reply to emails especially the ones specifically addressed to you. The sender is still waiting to hear from you.
8. Keep you email message short and to the point. Sentences like "I hope this email finds you alive and well" look good only in letter correspondence.
9. Do not hit the Send button without doing a spell check. An email with spelling mistakes or grammatical errors indicate that you have written the message in a non-serious mood and may convey a bad impression. Always read the message before broadcasting it to the world.
10. You may want to remove your personal mobile number and the home number from the email signature if you are participating in a big mailing list. You never know the kind of people who have subscribed to that list.
Brief Overview of Punctuation: Semicolon, Colon,Parenthesis, Dash, Quotation Marks, and Italics
Period
Use a period to end a complete sentence. A sentence is a group of words containing a subject and predicate. In British English a period is called a 'full stop'.
Examples:
He went to Detroit last week.
They are going to visit.
Comma
There are a number of different uses for commas in English. Commas are used to:
Separate a list of items. This is one of the most common uses of a comma. Notice that a comma is included before the conjunction 'and' which comes before the final element of a list.
Examples:
I like reading, listening to music, taking long walks, and visiting with my friends.
They would like books, magazines, DVDs, video cassettes, and other learning materials for their library.
Separate phrases (clauses). This is especially true after a beginning dependent clause or a long prepositional phrase.
Examples:
In order to qualify for your certificate, you will need to take the TOEFL exam.
Although he wanted to come, he wasn't able to attend the course.
Separate two independent clauses that are connected by a conjunction such as 'but'.
Examples:
They wanted to purchase a new car, but their financial situation would not allow it.
I'd really enjoy seeing a film this evening, and I'd like to go out for a drink.
Introduce a direct quote (as opposed to indirect speech i.e. He said he wanted to come ...).
Examples:
The boy said, "My father is often away during the week on business trips."
His doctor replied, "If you don't stop smoking, you run the risk of a heart attack."
Separate appositives (a noun, or noun phrase) or non-defining relative clauses.
Examples:
Bill Gates, the richest man in the world, comes from Seattle.
My only sister, who is a fantastic tennis player, is in great shape.
Question Mark
The question mark is used at the end of a question.
Examples:
Where do you live?
How long have they been studying?
Exclamation Point
The exclamation point is used at the end of a sentence to indicate great surprise. It is also used for emphasis when making a point. Be careful not to use an exclamation point too often.
Examples:
That ride was fantastic!
I can't believe he is going to marry her!
Semicolon
There are two uses for a semicolon:
To separate two independent clauses. One or both of the clauses are short and the ideas expressed are usually very similar.
Examples:
He loves studying; He can't get enough of school.
What an incredible situation; it must make you nervous.
To separate groups of words that are themselves separated by commas.
Examples:
I took a holiday and played golf, which I love; read a lot, which I needed to do; and slept late, which I hadn't done for quite a while.
They plan to study German, for their travels; chemistry, for their work; and literature, for their own enjoyment.
Colon
A colon can be used for two purposes:
To provide additional details and explanation.
Examples:
He had many reasons for joining the club: to get in shape, to make new friends, to lose some weight, and to get out of the house.
She gave notice for the following reasons: bad pay, horrible hours, poor relations with colleagues, and her boss.
To introduce a direct quote (a comma can also be used in this situation).
Examples:
He announced to his friends: "I'm getting married!"
She cried out: "I never want to see you again!"
Underlining and Italics
Underlining and italics are not really punctuation, but they are significant textual effects used conventionally in a variety of situations. Before computerized word-processing was widely available, writers would underline certain terms in handwritten or manually typed pages, and the underlining would be replaced by italics in the published version. Since word processing today allows many options for font faces and textual effects, it is generally recommended that you choose either underlining or italics and use it consistently throughout a given document as needed. Because academic papers are manuscripts and not final publications and because italics are not always easily recognized with some fonts, many instructors prefer underlining over italics for course papers. Whichever you choose, italics or underlining should be used . . .
for example:
to indicate titles of complete or major works such as magazines, books, newspapers, academic journals, films, television programs, long poems, plays of three or more acts
Faulkner's last novel was The Reivers.
The Simpsons offers hilarious parodies of American culture and family life.
Use a period to end a complete sentence. A sentence is a group of words containing a subject and predicate. In British English a period is called a 'full stop'.
Examples:
He went to Detroit last week.
They are going to visit.
Comma
There are a number of different uses for commas in English. Commas are used to:
Separate a list of items. This is one of the most common uses of a comma. Notice that a comma is included before the conjunction 'and' which comes before the final element of a list.
Examples:
I like reading, listening to music, taking long walks, and visiting with my friends.
They would like books, magazines, DVDs, video cassettes, and other learning materials for their library.
Separate phrases (clauses). This is especially true after a beginning dependent clause or a long prepositional phrase.
Examples:
In order to qualify for your certificate, you will need to take the TOEFL exam.
Although he wanted to come, he wasn't able to attend the course.
Separate two independent clauses that are connected by a conjunction such as 'but'.
Examples:
They wanted to purchase a new car, but their financial situation would not allow it.
I'd really enjoy seeing a film this evening, and I'd like to go out for a drink.
Introduce a direct quote (as opposed to indirect speech i.e. He said he wanted to come ...).
Examples:
The boy said, "My father is often away during the week on business trips."
His doctor replied, "If you don't stop smoking, you run the risk of a heart attack."
Separate appositives (a noun, or noun phrase) or non-defining relative clauses.
Examples:
Bill Gates, the richest man in the world, comes from Seattle.
My only sister, who is a fantastic tennis player, is in great shape.
Question Mark
The question mark is used at the end of a question.
Examples:
Where do you live?
How long have they been studying?
Exclamation Point
The exclamation point is used at the end of a sentence to indicate great surprise. It is also used for emphasis when making a point. Be careful not to use an exclamation point too often.
Examples:
That ride was fantastic!
I can't believe he is going to marry her!
Semicolon
There are two uses for a semicolon:
To separate two independent clauses. One or both of the clauses are short and the ideas expressed are usually very similar.
Examples:
He loves studying; He can't get enough of school.
What an incredible situation; it must make you nervous.
To separate groups of words that are themselves separated by commas.
Examples:
I took a holiday and played golf, which I love; read a lot, which I needed to do; and slept late, which I hadn't done for quite a while.
They plan to study German, for their travels; chemistry, for their work; and literature, for their own enjoyment.
Colon
A colon can be used for two purposes:
To provide additional details and explanation.
Examples:
He had many reasons for joining the club: to get in shape, to make new friends, to lose some weight, and to get out of the house.
She gave notice for the following reasons: bad pay, horrible hours, poor relations with colleagues, and her boss.
To introduce a direct quote (a comma can also be used in this situation).
Examples:
He announced to his friends: "I'm getting married!"
She cried out: "I never want to see you again!"
Underlining and Italics
Underlining and italics are not really punctuation, but they are significant textual effects used conventionally in a variety of situations. Before computerized word-processing was widely available, writers would underline certain terms in handwritten or manually typed pages, and the underlining would be replaced by italics in the published version. Since word processing today allows many options for font faces and textual effects, it is generally recommended that you choose either underlining or italics and use it consistently throughout a given document as needed. Because academic papers are manuscripts and not final publications and because italics are not always easily recognized with some fonts, many instructors prefer underlining over italics for course papers. Whichever you choose, italics or underlining should be used . . .
for example:
to indicate titles of complete or major works such as magazines, books, newspapers, academic journals, films, television programs, long poems, plays of three or more acts
Faulkner's last novel was The Reivers.
The Simpsons offers hilarious parodies of American culture and family life.
Shifts, Process, Support, and Callcenters
Shifts
1. Australian Shifts
2. US Shifts
3. UK Shifts
4. Day Shifts
5. Rotational Shifts
Process
1. In-Bound Process
2. Out-Bound Process
3. Surveys Process
Support
1. Customer Support Executives - (Non-Voice)
2. Customer Support Executives - (Voice)
3. Technical Support Executives - (Non-Voice)
4. Technical Support Executives - (Voice)
Call Center
1. Tamil Call Center Executives
2. Telugu Call Center Executives
3. Malayalam Call Center Executives
4. Kannada Call Center Executives
5. Hindi Call Center Executives
6. Customer Support Executives(Voice)
1. Australian Shifts
2. US Shifts
3. UK Shifts
4. Day Shifts
5. Rotational Shifts
Process
1. In-Bound Process
2. Out-Bound Process
3. Surveys Process
Support
1. Customer Support Executives - (Non-Voice)
2. Customer Support Executives - (Voice)
3. Technical Support Executives - (Non-Voice)
4. Technical Support Executives - (Voice)
Call Center
1. Tamil Call Center Executives
2. Telugu Call Center Executives
3. Malayalam Call Center Executives
4. Kannada Call Center Executives
5. Hindi Call Center Executives
6. Customer Support Executives(Voice)
Subscribe to:
Posts (Atom)